
As organizations strive to make their operations more agile in response to dynamic marketplace, they try to connect their Operational Technology (OT) systems to the Information Technology (IT) Infrastructure. Now, although there are significant benefits, such as access to real-time market data, major cost savings and effective and efficient monitoring of processes, this connection exposes OT systems to key security challenges. According to Fortinet’s 2019 Operational Technology Security Trends Report, 77% of OT leaders said they experienced a malware intrusion in the past year and half experienced between three and ten.
The Fortinet 2019 Operational Technology Security Trends Report analyzes data gathered from millions of Fortinet devices to discern the state of cybersecurity for ICS and SCADA systems.
Some of the key trends from the report indicate:
1. Increasing IT-based attacks impacting OT systems
With OT systems getting connected to IT networks, chances of more attacks increase. More and more cyber attackers target IT and OT systems at an organization simultaneously with the same malware. Since OT systems often use older technology and security operations are frequently less developed, the attackers have a higher rate of success there.
Malware recycling for OT
Cyber attackers are reusing legacy malware packages that were used in the past for IT attacks, but are now caught by any signature-based IT security solution. Figure 1 shows the percentage of existing threats detected by Fortinet during each month of the year, as well as the number of devices with OT protocols hit by any of the threats each month.
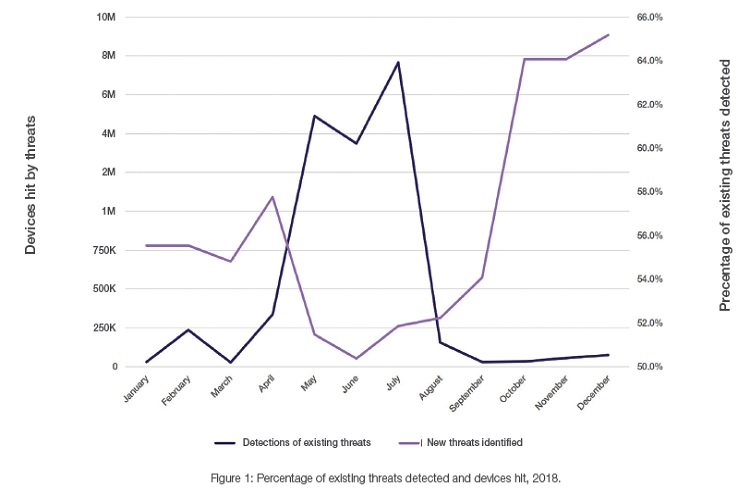
The figure shows that the pattern is very cyclical: when more threats are being used, fewer devices are hit, and vice versa. This cycle shows that adversaries are casting about for new vulnerabilities in newly connected OT systems. In the “reconnaissance” phase, they test a wider variety of old malware on a relatively small number of machines. Once they identify the threats that were successful, they move into an “attack” phase, using the subset of attacks that proved successful on a larger number of machines. Their aim is to maximize the value of existing malware before investing in creating new, more targeted attacks.
Another factor may also contribute to this seasonal variation in the use of new versus old threats. Specifically, attacks on heating, ventilation, and air conditioning (HVAC) systems and electrical grids are more likely to occur when these systems are operating at peak usage—most often during the Northern Hemisphere’s summer months. The age of an OT system is also a factor, with adversaries tending to target older technology more frequently than newer, more secure technology.
Cyber attackers targeting devices using variety of OT protocols
While IT systems have been standardized for many years on the TCP/IP protocol, OT systems use a wide array of protocols, many of which are specific to functions, industries, and geographies. The OPC Foundation was established in the 1990s as an attempt to move the industry toward protocol standardization. OPC’s new Unified Architecture (OPC UA) has the potential to unite protocols for all industrial systems, but that consolidation is many years away due to the prevalence of legacy protocols and the slow replacement cycle for OT systems.
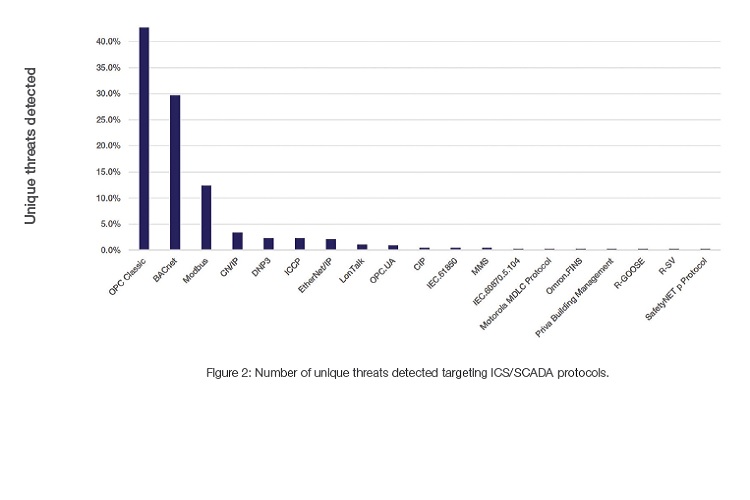
Cyber criminals have actively attempted to capitalize on this confusion by targeting the weak links in each protocol. These structural problems are exacerbated by the lack of standard protections and poor security hygiene practiced with many OT systems—a legacy of the years when they were air gapped. Figure 2 shows the number of unique threats targeting machines using specific ICS/SCADA protocols.
Despite seasonal fluctuations and a wide variety of targets, the data is clear on one thing: IT-based attacks on OT systems are increasing.
For example, Figure 1 shows that the spike in new threats detected is much higher at the end of the year than the spike at the beginning of the year.
2. Increasing Malware and Ransomware attacks targeting safety systems
Malware targeted specifically at ICS and SCADA systems has been developed for a decade or longer, but examples are not numerous. OT specific exploits include Stuxnet, Havex, Industroyer, and most recently, Triton/Trisis.
Ransomware also continued to attack OT systems. For instance, NotPetya Ransomware massively affected both IT and OT systems.
3. OT system attacks transcending geographically
In a global economy dominated in many industries by global players and characterized by extreme connectivity, geography is easy to traverse for legitimate actors as well as criminals. While attacks targeting most vendors were relatively level from region to region, Rockwell and Schneider exploits disproportionately affected North America, while Siemens attacks were more frequent in Asia Pacific. In all three cases, this reflects where the strong markets are for each company. On the other hand, Moxa systems are ubiquitous and heavily targeted around the world, despite the Japan-centric nature of the biggest attack on its users—the Moxa 313 vulnerability.
While the BACnet and Modbus protocols were heavily targeted around the world, EMEA saw the most intense level of detections. The volume of attacks on machines using the other protocols was either fairly level across geographies or more focused in the areas where they are most commonly used. For example, ICCP is primarily used by vendors such as Siemens and Honeywell, which have a smaller footprint in Asia.
Therefore, a threat landscape should be taken seriously by any organization that has connected ICS/SCADA systems as these have historically been the technology workhorses at many organizations, lasting for decades without major upgrades. The reality of advanced persistent threats requires a more strategic approach—everything from patching to segmentation to access control. It is imperative that those systems are subject to the same level of security protection, the same security hygiene standards, and the same tracking and reporting processes as the IT network. Otherwise, the OT network will be the weak link through which adversaries are able to infiltrate and gain access to critical systems and data—both OT and IT.
To make this happen, the IT and OT functions in every organization need to overcome the cultural challenges brought on by their past isolation.
The groups must come to understand each other’s values so that a mutually beneficial relationship can be forged for the future. The threats are real, and they will get bigger. The best way to counter them is with a comprehensive, strategic approach involving an entire organization.

 In
In
Comments
Levitra Ohne Rezept Schweiz
Levitra Ohne Rezept Schweiz https://buyciallisonline.com/ - Buy Cialis Purchase Isotretinoin Price In Internet <a href=https://buyciallisonline.com/#>Cialis</a> Mer
Levitra Ohne Rezept Schweiz
Levitra Ohne Rezept Schweiz https://buyciallisonline.com/ - Buy Cialis Purchase Isotretinoin Price In Internet <a href=https://buyciallisonline.com/#>Cialis</a> Mer
Levitra Ohne Rezept Schweiz
Levitra Ohne Rezept Schweiz https://buyciallisonline.com/ - Buy Cialis Purchase Isotretinoin Price In Internet <a href=https://buyciallisonline.com/#>Cialis</a> Mer
Amoxicillin For Fish https:/
Amoxicillin For Fish https://agenericcialise.com/ - Generic Cialis cialis viagra generico <a href=https://agenericcialise.com/#>cialis otc</a> drug interaction lisinopril and cialis
Amoxicillin For Fish https:/
Amoxicillin For Fish https://agenericcialise.com/ - Generic Cialis cialis viagra generico <a href=https://agenericcialise.com/#>cialis otc</a> drug interaction lisinopril and cialis
Progesterone Website Secure
Progesterone Website Secure Ordering https://bbuycialisss.com/ - Cialis Cialis Canadian Ph <a href=https://bbuycialisss.com/#>Buy Cialis</a> Hydrochlorothiazide Express Delivery Store
Progesterone Website Secure
Progesterone Website Secure Ordering https://bbuycialisss.com/ - Cialis Cialis Canadian Ph <a href=https://bbuycialisss.com/#>Buy Cialis</a> Hydrochlorothiazide Express Delivery Store
Tadalis Sx Soft Online
Tadalis Sx Soft Online Discount Velabeibly https://ascialis.com/# - order cialis online Keyday Zithromax Penicillin Allergy elopleseni <a href=https://ascialis.com/#>Cialis</a> JarInfor Viagra Beneficios
Tadalis Sx Soft Online
Tadalis Sx Soft Online Discount Velabeibly https://ascialis.com/# - order cialis online Keyday Zithromax Penicillin Allergy elopleseni <a href=https://ascialis.com/#>Cialis</a> JarInfor Viagra Beneficios
Add new comment