
The recent data breach incident involving the CoWIN platform, India's primary platform for managing COVID-19 vaccination appointments, has sparked a heated discussion on digital security. As investigations continue, cybersecurity experts have provided valuable insights into the breach, shedding light on its methodology and the origins of stolen data and offering recommendations to bolster digital security.
Breach analysis: Unauthorized access and phishing attacks
Initial analysis by cybersecurity experts suggests that the CoWIN data breach may have occurred through unauthorized access to individuals' devices or via phishing attacks. Instead of directly targeting the CoWIN platform, the breach exploited vulnerabilities in endpoints, highlighting the importance of securing devices and raising awareness about potential risks associated with sharing personal information with unknown sources.
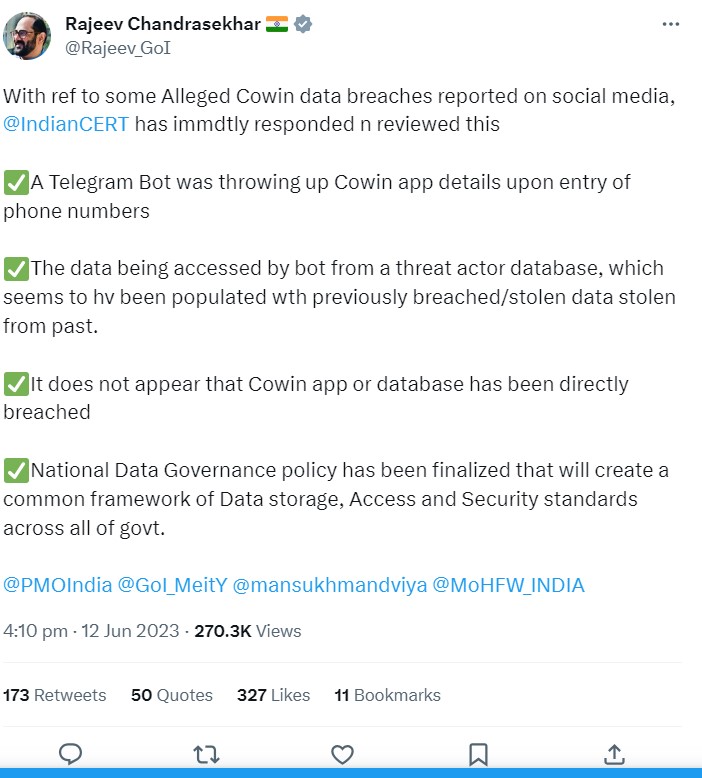
Experts hint at previously stolen data
In an exciting twist, experts have hinted at the possibility of the leaked data being sourced from previous breaches. This suggests that the attackers may have acquired personal information from other platforms and then correlated it with CoWIN records. This revelation underscores the need for robust data protection measures across various platforms to prevent the misuse of personal data.
Experts call for transparency and incident response
Cybersecurity experts have commended the government's prompt response to the breach, including initiating an investigation and enhancing security. However, there is a growing demand for increased transparency in communication regarding the details of the breach, steps taken to address the issue, and measures implemented to prevent future incidents. Transparency is crucial in maintaining public trust and ensuring citizens are informed about the actions to safeguard their data.
Impact of the data leak
The data leak could have several negative consequences. It could lead to identity theft, fraud, and other crimes. It could also damage public trust in the CoWin platform and the Indian government.The government has taken steps to mitigate the impact of the data leak. It has said it will provide free credit monitoring to those affected. It has also said that it will strengthen the security of the CoWin platform. However, it is too early to say what the long-term impact of the data leak will be. It may have a lasting impact on the Indian government's ability to deliver its vaccination program.
Key Insights: Strengthening Digital Security Measures
In light of the CoWIN data breach, cybersecurity experts have provided key recommendations to enhance digital security:
Multi-factor Authentication (MFA): Implementing MFA as an additional layer of security can significantly reduce the risk of unauthorized access. By requiring users to provide additional authentication factors, such as one-time passwords or biometric verification, MFA adds an extra barrier against potential breaches.
Endpoint Security: Focusing on securing endpoints, such as mobile devices and computers, is vital. Employing robust antivirus software, regularly updating operating systems and applications, and educating users about potential risks associated with downloading malicious software or clicking on suspicious links can help prevent breaches.
Regular Security Audits: Regular security audits allow organizations to identify and address vulnerabilities promptly and proactively. Identifying gaps in the system and implementing necessary patches, updates, and security controls can mitigate potential threats effectively.
Encrypted Data Transmission: Encrypting data during transmission adds a layer of security, ensuring that the information remains unreadable to unauthorized individuals even if intercepted. Secure communication protocols, such as HTTPS, protect against data interception and tampering.
User Awareness and Training: Educating users about cybersecurity best practices is crucial. Training programs should cover topics such as recognizing phishing attempts, creating strong passwords, avoiding suspicious websites, and being cautious about sharing personal information online. This empowers users to play an active role in safeguarding their data.
Conclusion
The CoWIN data breach has brought digital security concerns to the forefront, prompting cybersecurity experts to analyze the breach and offers valuable recommendations. What specific measures will the government take to strengthen the security of the CoWIN platform? How many individuals were affected by the data breach, and what specific personal information was compromised? Will the CoWIN platform be temporarily shut down or modified in any way due to the breach?
Securing endpoints and raising user awareness becomes paramount With the breach attributed to unauthorized access and phishing attacks. Additionally, the revelation of previously stolen data being potentially used highlights the need for stringent data protection measures across platforms. By implementing recommended security measures, such as multi-factor authentication, endpoint protection, regular security audits, encrypted data transmission, and user education, organizations can bolster their defenses and ensure a more secure digital landscape. Transparency in incident response is also critical to maintaining public trust and keeping citizens informed about efforts to safeguard their data.
By analyzing the breach methodology, identifying the origins of stolen data, and providing valuable recommendations, experts emphasize enhanced security practices, such as multi-factor authentication, endpoint protection, regular security audits, encrypted data transmission, and user awareness and training. By implementing these measures, organizations can strengthen their defenses and safeguard personal information, ensuring a more secure digital landscape.

 In
In
Add new comment