
Over the last few years, social media has witnessed a steep rise in cryptocurrency scamming. The widespread hacking of prominent personalities in July 2020 is one such incident arising due to a Bitcoin giveaway scam on Twitter. What set this attack apart was that it managed to leverage a lot of big names to execute it.
To execute this attack, a cryptocurrency give-away scam was setup, and to promote this campaign a website with a domain name ‘CryptoForHealth’ was registered on 15th of July 2020 according to the Internet Corporation for Assigned Names and Numbers. This site is currently flagged as a phishing site and has now been taken down.
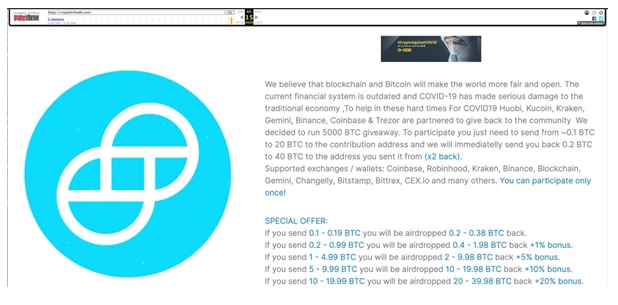
To promote this fraudulent scheme, hackers did meticulous planning. They hackers initially hacked into twitter accounts of all the top crypto exchanges like Coinbase, Binance, Kucoin, Coindesk etc. and individual crypto influencers like Justin Sun, Charlie Lee, King Cobie, AngeloBTC among others. Identical tweets were posted via all these hacked accounts claiming a partnership with CryptoForHealth, offering to give away 5000 Bitcoins to their followers.
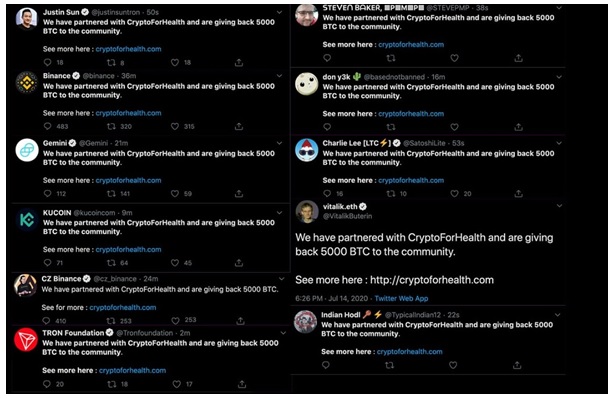
On 16th of July 2020, Twitter accounts of many renowned individuals and organizations were hacked by alleged Bitcoin fraudsters to create more impact. The renowned entities include Jeff Bezos, Bill Gates, Elon Musk, Kanye West, Joe Biden, Kim Kardashian, Apple’s official account, and many others. Other non-verified accounts also posted similar tweets, although it is not clear if those accounts were also hacked or were merely bots.
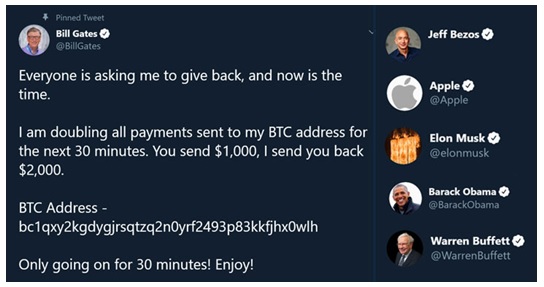
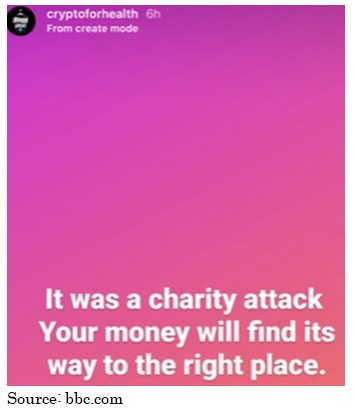
The hackers posted charitable tweets from the hacked accounts, saying they would ‘Double the money sent to the bitcoin account’. The hack has been followed by an Instagram update by the apparent hackers that ‘the money will reach its right place’.
This has raised apprehensions about Twitter’s cyber safety mechanisms. Twitter is one of the most used platforms by eminent politicians and business folk. In the backdrop of this attack, it is to be noted that U.S. Presidential elections are around the corner. India houses the largest number of Internet users in the world. It is extremely crucial for the agencies to understand such attacks and create a cybersecurity policy in anticipation of any such attack on Indian entities.
This article aims to elaborate the details of the attack, along with the possible methodology used by the hackers.
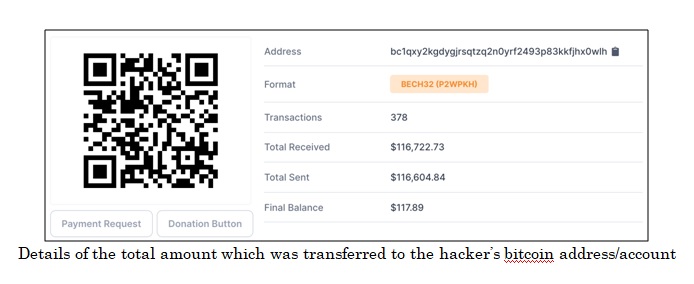
There are a few generic observations about the attack, which are imperative to understand the gravity of the cybersecurity scenario across the globe. Around USD 116722.73 was transferred to the bitcoin address ‘bc1qxy2kgdygjrsqtzq2n0yrf2493p83kkfjhx0wlh’. A total of 378 users transferred bitcoins to this address to get it doubled. Around USD 116604.84 has been sent from the hacker's primary account to another Bitcoin address, which could be the address of the mastermind of the entire attack. The last transaction was done after it was revealed that Bill Gates’ and other renowned entities’ accounts were compromised.
Attackers might have used a particular approach for this attack, which is easy to discern, but the magnitude of the attack makes it dangerous. There seems to have been a lack of proper security controls while twitter allowed its employees to work from home. A series of social engineering attempts of twitter employees which were successful led the hackers to trace them. The security controls Twitter uses while it allowed users to work from home were not complex and hacker could understand the entire complexity and the network system deployed.
Series of privilege escalation techniques were used to gain meaningful administrative level access, control of Twitter’s internal tools and bypass security controls. Successful compromise of the VPN server of Twitter led to the access and eventual hacking of celebrity and high net worth individual accounts which was further utilized to launch massive tweets by automated tools.
This episode mandates a few crucial lessons to be learnt by organizations to safeguard themselves against similar attacks possible in the future. Proper implementation of effective ‘work from home’ security solutions for the organization is a must while employees have to work from home. Training the employees on how to safeguard themselves from Phishing attacks and create reporting mechanism for employees to flag any malicious attempts becomes imperative. Companies must also use multifactor authentication solutions to allow access to applications, systems that hold confidential and critical data.
As a matter of practice, regular vulnerability assessment and penetration testing of the network which allows work from home must be carried out. Suitable and effective end point security controls must be deployed on systems which people are using to work from home. Their monitoring must be done through behavioral anomaly based detections solutions.
Going forward, it is important to carry out regular Cyber Threat intelligence and Cyber Threat Hunting activities to monitor threat actors targeting an organization, and also to find out insider threats. The Cybersecurity ecosystem is clearly compromised in the age of Industry 4.0. It needs an overhaul and an effective, coming-of-age mechanism to root out any such attacks being planned in the future. This is necessary to maintain the credibility of the online world and keep the digital ecosystem functioning smoothly.
The author is Founder of India Future Foundation

 In
In
Add new comment