
The annual Global Risk Report (GRR) of Geneva-based global think tank, the World Economic Forum (WEF), based on its Global Risk Perception Survey, is arguably the most important current risk assessment statement at a global level. This report hugely influences the risk planning strategy of global businesses, financial institutions and world governments.
In this year’s GRR, two cyber security risks—data fraud/theft and cyberattacks—were identified as two of the five most likely risks for 2019, next only to extreme weather events, future of climate change mitigation & adaptation and natural disaster—and ahead of such risks as man-made environmental disasters, large-scale involuntary migration, biodiversity loss and ecosystem collapse, water crises and asset bubbles in a major economy.
The WEF GRR also ranks the risks in terms of impact. Cyberattacks was ranked as the seventh most impactful risk, along with such risks as weapons of mass destruction, extreme weather events, future of climate change mitigation & adaptation, and natural disasters.
According to the GRR 2019, a large majority of respondents expected increased risks in 2019 of cyberattacks leading to theft of money and data (82%) and disruption of operations (80%). Around two-thirds of respondents expect the risks associated with fake news and identity theft to increase in 2019, while three-fifths said the same about loss of privacy to companies and governments.
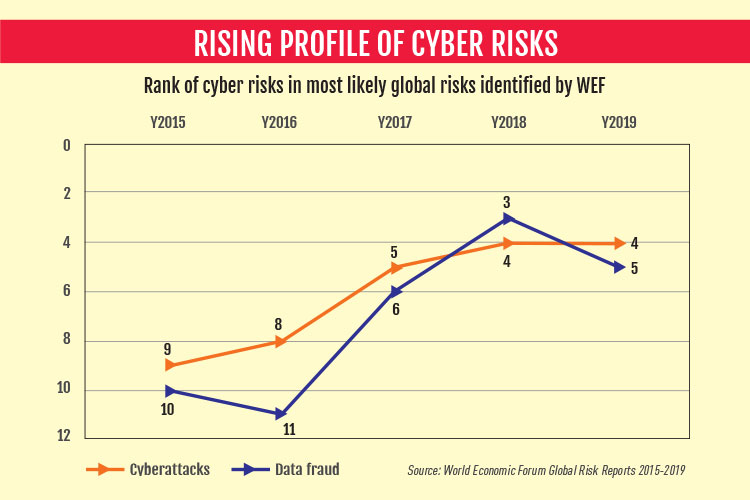
The 2019 report is not an isolated example of a GRR counting cyber risks among the top global risks. The likelihood of cyber risks has consistently gone up in the WEF annual surveys. In 2015, data fraud ranked as the 9th most likely global risk in the year’s GRR. It has consistently risen as a risk to rank as the 4th most likely this year. Similarly, just three years back—in 2016, cyberattacks were seen as the 11th most likely risk, which is today ranked as the fifth most likely. In short, the high likelihood factors associated with cyber risks are not an accidental one-off phenomenon; its rise as a global risk has been gradual and consistent.
Cyber risk as a corporate risk
While the GRR tries to assess the risk from the point of view of a broader global community—that includes governments, multilateral agencies and financial institutions—how serious are the businesses about cyber risks.
A survey conducted in 2018 by insurance broking and risk management company Marsh and IT major Microsoft shows how companies see the seriousness of cyber risk. According to the Marsh-Microsoft Cyber Perception Survey,nearly two-thirds of survey respondents see cyber risk being among their organization’s top five risk management priorities. That is roughly double the percentage who rated cyber that high in a survey Marsh conducted in 2016. From the companies that the research covered, 56% ranked cyber security risks among their top five risks and a small but significant number—6% of all companies—ranked it as the biggest risk!

No wonder, they have started quantifying the financial cost of major cyber incidents.
From among the USD 1 billion dollar-plus companies, as many as 42% estimate the worst potential value of financial loss in case of an incident to be more than USD 50 million, out of which two-third estimate the loss to be more than USD 100 million.
A new Aon report puts a number to the magnitude of the aggregate losses. It estimates annual global cyber losses are expected to hit USD 6 trillion by 2021, with cybersecurity spending projected to exceed a total of USD 1 trillion for the five years leading up to 2021.
The report, ‘Prepare for the unexpected: Safeguarding value in the era of cyber risk’, notes that while the immediate costs of a cyberattack can be significant, damages to a business’s reputation could cost just as much or even more in the long-term.
According to a research published in June this year by ESI ThoughtLab, on an average, annual losses from cyberattacks grew to USD 4.7 million last year—with more than one in 10 companies losing more than USD 10 million. That amount equates to an average of 0.114% of revenue across all firms surveyed.
Are cyber risks too serious to be left to the techies?
As we have seen in many cases—including the rollout of digital strategies in organizations and transformation to data-driven business models—when something becomes too important, people turn to newer more specialized workforce or push the responsibility upwards.
Is cyber security too becoming too important to be left to the custodians of technology—the IT department?
Answer is a clear and resounding No. Maybe because of the specializations involved as well as lack of enough manpower, organizations are not taking away cyber security responsibility from the IT guys—the CIOs and CISOs, even among the largest of organizations.
According to the Marsh-Microsoft survey, as much as 77% of respondents from more than USD 5 billion plus companies said IT is the primary owner and decision maker for cyber risk management in their organization. For companies between USD 1 billion and USD 5 billion in revenue, that number rises significantly to 83%.
What it means is:
1. Organizations have begun to recognize the seriousness of cyber risks and have even stared assessing it financially.
2. They have most decisively shown that they will continue to expect the management of that risk from their IT guys—the CIOs and CISOs.
The CISO challenges
The rising profile of cyber risk is significantly due to the rise in complexity and sophistication of cyber risks.
“Today, attackers have reached a certain level of maturity and efficiency. They are taking advantage of the increased value and vulnerability of online targets that is resulting in a dramatic increase in attack frequency, complexity and size,” says Sheril Jose, Head - Cyber Security at Pune-based Emcure Pharmaceuticals.
Vijay Radhakrishnan, CISO of Mahindra & Mahindra Financial Services adds to this explaining, “New threats are comprehensive, intelligent and are highly stealthy. While threat assessment, monitoring and attack curtailment have gone in the direction of big data analytics, ML, AI and blockchain way, hackers work in similar war filed and are well financed to do so. It’s almost cyber militancy which is managed on a daily basis.”
How significant is the challenge for India? The average value of loss reported by the ESI ThoughtLab research quoted above across countries shows that at an average of more
than USD 6.5 million, the value is second highest for Indian companies, closely behind the average value of loss reported for German companies
and significantly higher than the average loss of companies in the US, China, France, the UK and Japan.
Quick Heal’s ‘Annual Threat Report 2019’ gives a more detailed view of Indian cyber security landscape. It states that most CISOs in India are grappling with newer issues, such as cryptojacking, ransomware and threats to mobile devices that were unheard even five years ago. With the increased use of new technologies, such as Artificial Intelligence (AI), Blockchain and the Internet of Things (IoT) in the enterprise, as well as increased popularity of digital transactions in recent years, CIO/CISOs must adopt innovative techniques to manage the escalated threats.
However, these are not problems specific to India, as the country is part of the connected global ecosystem, where advanced persistent DDoS campaigns are now the norm. Also global growth of IoT devices is becoming great breeding ground for hackers to enslave more and more devices. To further complicate things, attackers are taking advantage of SSL-encrypted traffic to camouflage their attacks, making it hard to determine malicious versus legitimate traffic.
While the average cost of breaches is humongous, the most challenging part is budget and skill constraints. There’s also lack of support from senior management, preventing CISOs from implementing a cohesive cybersecurity strategy.
“The CISO has to ensure that controls are implemented in the right manner within the organization and they are based on the results of risk assessment and not on the decisions of functions,” says Meetali Sharma, Corporate
Risk, Compliance & Security Leader at SDG Software India.
“Also with so many products in the market, one of the key security challenges is to ensure that you pick the right tools/technologies for your organization based on the need of the organization and not just because it is a fancy tool and gives nice dashboards,” she adds.
Gearing up against cybercrime
To fight against cybercriminals, firms are investing more in their cybersecurity budgets from what they did in the past. CISOs now have a huge responsibility to continually assess the security tools and processes they’ve put in place in their organizations to prevent a breach or cyber attack. To be ahead of the game, CISOs are continuously reviewing their cybersecurity processes and practices to ensure that adequate and effective systems are in place.
Integrating security and business risks management
A recently released ‘Cisco 2019 CISO Benchmark Study’ observes that CISOs are modifying and expanding their security strategies to address new and emerging security threats. Nearly half of the survey’s respondents (47%) report that they are now using outcome-based objectives to focus on their security spending. For instance, many companies are investing in threat intelligence programs that are helping them identify, prevent and respond to these threats through informed decisions.
Wendy Nather, director of advisory CISOs at Duo Security, a Cisco unit, mentions in the report that CISOs are making sure that the results are tangible. “In terms of strategy, the vast majority of organizations (94%) are practicing incident response at least once a year; 61% are doing it at least every six months. “These exercise drills are helping enterprises develop the skills they need to face evolving security threats,” she says.
It is important to integrate security and business risk management. “Cybersecurity is not an isolated aspect of an organization. Its impact goes beyond IT and can have serious legal and reputational implications. IT security, then, should not be detached from the wider business risk management strategy,” says Makarand Sawant, Senior General Manager - IT, Deepak Fertilisers and Petrochemicals Corporations Limited.
Focus on better IT governance
There is also increased focus on better IT governance, as new challenges stemming from the increasingly complex regulatory environment, including new regulations (like GDPR and Indian Data Protection Act) are evolving, and enhancements to existing regulations are coming up, thereby forcing organizations to comply with it.
“It is very important to carefully keep monitoring your controls and harmonizing them. A new control should not be implemented to meet a new regulatory requirement, rather, one should try to reuse and enhance an existing control based on the changing needs. An organization’s security framework should be extensible enough to accommodate such changes in this agile regulatory environment,” Sharma says.
A 2018 ISACA report found that IT governance is essential to strong business performance and is now a board-level priority. It recommends CISO/CIOs and boards should define an appropriate set of security policies and associated procedures and security architectures for each business risk.
Greater collaboration and communication
Gap in communication is a major barrier in the direction of effective security. Despite having a solid security framework in place, lack of collaboration at the C-suite has been found to jeopardize cybersecurity in organizations. A recent report by Accenture found only 40% of the CISOs surveyed said that they always confer with business-unit managers to understand the business before proposing a security approach, pointing at a shortage of ongoing communication and lack of trust.
“A better engagement between CEOs, board members, and CISOs or CIOs will result in a fine-tuned and effective cyber risk mitigation strategy,” says Sawant.
“CISOs and CIOs need to work with their C-suite colleagues and board directors to bring governance practices into the digital age. Now that boards are accepting that cyber risk management and regulations require their oversight as much as any other business risk, it is time security leaders become more vocal about their task at hand,” agrees Jose.
“In such a scenario, security leaders need to keep abreast of the latest threats and prepare for the outcome of every strategy. Security should in fact be the board’s top priority and the management should take it very seriously. Adoption of best in grade technology is important for every organization. CIO/CISO needs to constantly communicate the same to the C-suite,” Radhakrishnan of Mahindra & Mahindra Financial Services says.
The Marsh-Microsoft survey found 45% of risk and technology executives saying that they send information on cyber investment initiatives to board members, while only 18% directors say they receive it. That is a big communication gap.
Training and enablement
The impact of the talent and skills shortage is also profound within today’s organizations. This shortage can prohibit strategic goals and leave businesses at risk. A Forbes Insights and Fortinet survey, titled ‘Making Tough Choices: How CISOs Manage Escalating Threats and Limited Resources’, states, security leaders are currently allocating an average of 36% of their security budget on response. However, in an ideal world, they would shift their resources from prevention to bolster detection and response. It is in this context that CISOs are paying more attention to educating their own employees on best practices and building cybersecurity awareness in order to prevent and reduce internal threats.
As per the ‘2019 Verizon Breach Investigations Report’, about 52% breaches featured hacking and close to 34% attacks involved inside actors. In order to best respond to threats, security leaders must focus on talent, team training, and strategy implementation.
“Since a lot of ransomware and phishing attacks are planned attacks and the root cause is employees in most of the cases, it is very important to ensure that adequate education and awareness is given to employees to make them a part of all the information security initiatives. Each employee should be a co-owner of security within the organization and should understand its importance,” recommends Sharma.
The road to confidence
Top priorities for many CISOs in the coming year will be to enable an enterprise-wide holistic security approach and hire more cybersecurity staff, as the Fortinet report suggests. In 2020, 14% of CISOs will dedicate priority funding to adding more security personnel to their teams. Additionally, over the course of the next five years, 16% of CISOs aim to develop a culture of security throughout their entire enterprise.
Despite taking tangible steps to reduce cybersecurity risks, cybersecurity continues to be an ever-evolving struggle for organizations. Sophos in its research report, titled ‘The Impossible Puzzle of Cybersecurity’, clarifies that there are ‘always’ some security holes not being plugged and it is here that CISOs need to pay greater attention. For example, the report explains, an up-to-date malware signature list won’t stop attackers hijacking your accounts, while rock-solid authentication won’t help if you’re not protecting your computers from ransomware.
“Good cybersecurity demands defense in depth and proper risk assessment so that you can protect your weakest spots from attack first,” says Chester Wisniewski, principal research scientist at Sophos.
At the same time, companies are facing attacks via multiple channels, including email, web and app-based platforms, among others. Software vulnerabilities and unauthorized USB sticks or other external devices were also common attack vectors. Sometimes, organizations are also not aware that their networks were compromised.
Good news is, Wisniewski believes,seasoned CISOs know that a good digital defense is not enough, so they are building a multilayered approach that includes stronger investment in people and process. Recognizing that some hackers will inevitably find a way in, CISOs are recalibrating their cybersecurity budgets to focus more on remediation. And many CISOs believe that their investments are already paying off.
To stay ahead of the game, companies need to stay vigilant everywhere, since attackers are relentless in exploiting weaknesses. With limited budgets, and cyber risks mushrooming, it is paramount that organizations understand the ROI of cybersecurity so that they invest in those efforts that will result in maximum outcome. By being prepared yet flexible and implementing new and innovative techniques, CISOs will enable a scalable defense fit to counter the breaches ahead of them.

 In
In
Add new comment