
Email is still the initial entry point into an organization for targeted attacks, the email-attack vector delivered malicious payloads to organizations in 2015, with a focus on Office documents and zip files, says recently released 2016 Global Threat Report published by security vendor Forcepoint Security Labs.
The report says Forcepoint found a 250% increase in malicious content in email in 2015, as compared to 2014. Dridex27 (a strain of banking malware) and various ransomware campaigns were largely responsible for the rise, the report concluded.
Email and web attack vectors had a significant convergence in 2015, with nine out of 10 unwanted emails containing a URL, says the report. Quoting the Identity Theft Resource Center’s 2015 Data Breach report, Forcepoint report says accidental email/Internet exposure was 2015’s third most common cause of compromised data, underscoring the importance of threat analysis across both attack vectors.
The report shares some relevant statistics. It says
- 91.7% of unwanted email contains a URL.
- 2.34% of unwanted email contains an attachment.
- Malicious macros in emails attachments up 44.7%
- 68.4% of email is spam (down from 88.5% in 2014)
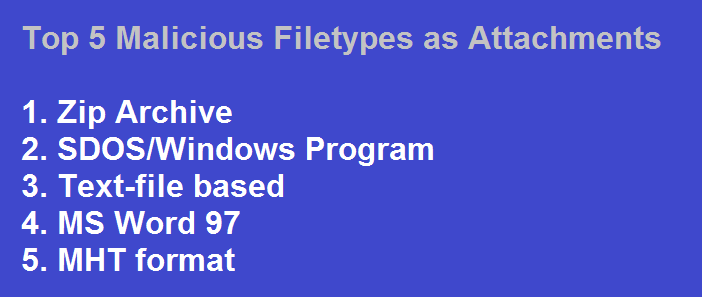
Forcepoint data suggests that malicious macros embedded into Microsoft Office file types were a prominent attack-delivery mechanism in 2015. Zip file attachments were the single largest malicious attachment file type.
The US remained the top country in terms of hosting maiicious content. It also topped the list of countries hodting phishing websites. It hosted more such sites than the next seven such countries put together.

Last year’s Threat Report revealed three million malicious macros observed over a thirty-day period at the end of 2014. In performing a similar sampling period at the end of 2015, Forcepoint found more than four million macros, up 44.7% from 2014.

Among other findings, the report said more than 80% of IT decision-makers feel shadow IT poses a risk to IT security, with a third considering it an extremely significant risk and 16% considering it the most significant risk. However, only 34% of those using shadow IT believe it poses a risk to security, with more than half citing that its use allows business departments to be more productive. Unfortunately, when IT can’t see data, it also can’t adequately protect it, creating the perfect environment for data to be lost or stolen, says Forcepoint
Articulating the significance of insider threats, Forcepoint report says that its own and third-party research shows that policing insider activity and accounting for privileged credentials are security issues organizations feel least-prepared to confront. A full 30% of security remains focused on perimeter defenses1, with less than 40% of organizations surveyed having dedicated budget to insider threat programs. Yet, many employees are empowered to connect remotely and are on and off networks constantly accessing servers (where your most sensitive data lives).

 In
In
Add new comment